Remotely SSH To IoT Device AWS Example: Keeping Your Connected Gadgets Accessible
Imagine your smart devices, scattered far and wide, needing a little bit of attention. Maybe a quick fix, a software tweak, or just a check-up. That, you know, can be a real head-scratcher when they're not right there in front of you. Getting to these gadgets, especially when they are part of a bigger network of connected things, often means you need a clever way to reach them from a distance. It's a common situation for anyone managing these kinds of systems, and finding a secure, straightforward method is pretty important.
This challenge gets even more interesting when you think about how many devices are out there, doing all sorts of jobs. From little sensors in a field to big machines in a factory, being able to peek inside and make changes without physically going to each one saves a lot of time and effort. It’s about keeping everything running smoothly, even when your devices are in remote spots or inside secure networks, so, it's almost like having a secret backdoor that's totally safe.
We’re going to look at how you can do just that, using a practical approach with AWS. This guide will walk you through the steps for a remotely ssh to iot device aws example, helping you understand how to securely connect to your IoT gadgets, wherever they might be. You'll see how AWS provides some neat tools to make this happen, keeping your data and devices safe while giving you the access you need, that is, pretty handy.
- Donald Trump As A Child
- Sophie Rain Look Alike
- Tom Hiddleston Personal Life
- What Does Bop Mean
- Destinys Child Cowboy Hat
Table of Contents
- Why Remote Access for Your IoT Devices?
- AWS and Secure IoT Access: A Closer Look
- Getting Started: Setting Up Your Remote SSH Connection via AWS
- Keeping Things Safe: Best Practices for Remote SSH
- Common Hurdles and Simple Solutions
- Frequently Asked Questions
- Final Thoughts on Remote IoT Access
Why Remote Access for Your IoT Devices?
Having the ability to connect to your IoT devices from a distance isn't just a nice-to-have; it's practically a necessity these days. Think about it: once you've deployed these little helpers out into the world, you can't just pick them up every time something needs adjusting. Remote access, like using SSH, provides a direct line to the device's inner workings, and that, you know, makes a big difference.
Troubleshooting from Afar
Devices, like any piece of tech, can sometimes act up. A sensor might stop sending data, or a small program might crash. When this happens, being able to log in remotely and check the logs, restart a service, or even run some diagnostic commands saves you a trip. It means you can figure out what's wrong and fix it without having to physically visit the device, which, as a matter of fact, is incredibly convenient.
Updates and Maintenance
Software gets better over time, and new features or security improvements come out regularly. Your IoT devices need these updates to stay current and safe. Remote access lets you push out new software versions, apply security patches, or even change configurations without ever touching the device. This keeps your entire fleet up-to-date and performing well, so, you could say it's like a remote tune-up.
- My 600 Lb Life Tiffanys Story
- People Born On June 27
- Cama King Dimensiones
- How Tall Is Jameliz
- Snow Peas Uk
Cost Savings and Efficiency
Every time you send a technician to a remote site to check on a device, it costs money and time. Fuel, wages, travel time – it all adds up. With remote access, many of these issues can be resolved from your desk. This drastically cuts down on operational costs and lets your team focus on more complex tasks, that is, a pretty smart way to manage things.
AWS and Secure IoT Access: A Closer Look
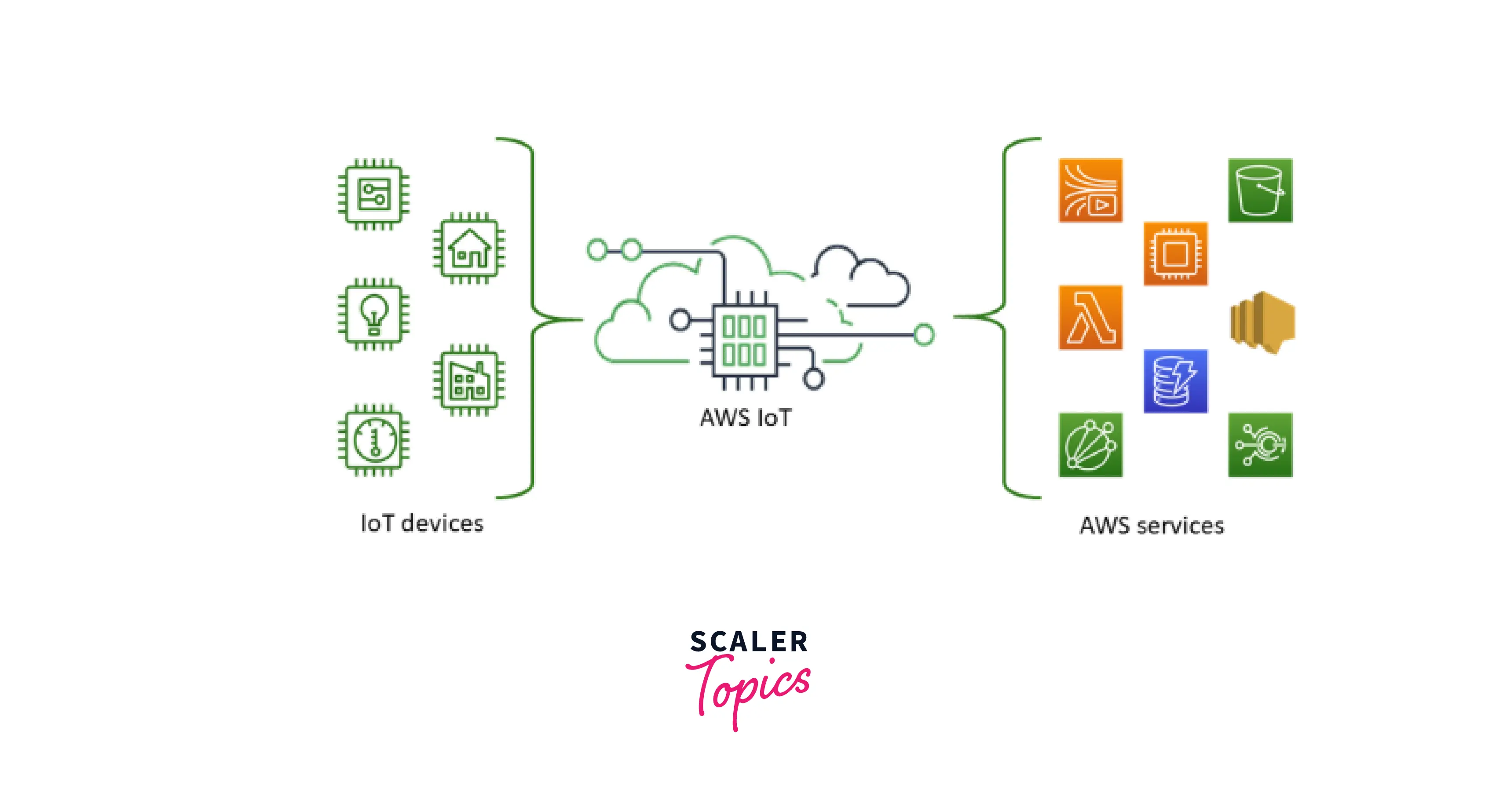
AWS offers a whole set of tools designed to help you manage your IoT devices, and making sure you can reach them securely is a big part of that. They've built services that understand the unique needs of connected devices, like their often limited processing power or intermittent network connections. When you think about a remotely ssh to iot device aws example, you're really looking at how these services work together, you know, to create a safe pathway.
The Role of AWS IoT Core
AWS IoT Core is the heart of AWS's IoT offerings. It's a managed cloud service that lets connected devices talk to cloud applications and other devices securely. It handles billions of messages and can route them to various AWS services. For our purpose, IoT Core helps manage the identity of your devices and ensures that only authorized devices can connect and communicate, which, in some respects, is like a bouncer for your devices.
Introducing AWS IoT Secure Tunneling
This is where things get really interesting for remote SSH. AWS IoT Secure Tunneling is a feature of AWS IoT Device Management that allows you to create a secure, two-way communication tunnel to your remote devices, even if they're behind firewalls or NATs. It doesn't require opening inbound ports on the device, which is a big security win. It works by setting up a secure channel through AWS, allowing you to then use standard tools like SSH over that channel. It's a very neat solution for a remotely ssh to iot device aws example, basically, because it keeps things private and safe.
The tunnel acts as a proxy. Your local SSH client connects to a local proxy, which then sends the data through the secure tunnel established by AWS IoT. On the device side, a small client (the destination client) receives the data and forwards it to the SSH daemon running on the device. This means your device doesn't need a public IP address or open ports, which is a significant security improvement, and that, you know, is pretty important for IoT.
Getting Started: Setting Up Your Remote SSH Connection via AWS
Now, let's get down to the practical steps for a remotely ssh to iot device aws example. Setting this up involves a few stages, from preparing your device to configuring AWS services. It might seem like a lot at first, but each step is pretty straightforward once you get the hang of it. We'll focus on using AWS IoT Secure Tunneling, which is a modern and secure way to achieve this, you know, without too much fuss.
What You'll Need
- An active AWS account.
- An IoT device (like a Raspberry Pi or an embedded Linux board) with an SSH server installed and running.
- Basic knowledge of Linux commands.
- An SSH client on your local machine.
- The AWS CLI installed and configured on your local machine.
- The AWS IoT Device SDK or a similar tool to run the destination client on your device.
Step 1: Prepare Your IoT Device
First things first, your IoT device needs to be ready to accept SSH connections. Make sure the SSH server (usually OpenSSH) is installed and active on your device. You'll also want to create a dedicated user account for remote access, rather than using the 'root' user, for security reasons. Also, ensure your device has network connectivity to AWS IoT Core. This is a basic but very important step, so, double-check everything here.
You might also need to install the AWS IoT Device SDK or a specific tunneling agent on your device. This agent will act as the "destination client" for the secure tunnel, listening for incoming connections from AWS IoT and forwarding them to your device's SSH port. You know, it's like a little helper program.
Step 2: Configure AWS IoT Core
Your device needs to be registered with AWS IoT Core. This involves creating an IoT "Thing" for your device, attaching a certificate to it, and creating an IoT policy that grants the necessary permissions. The policy needs to allow actions related to secure tunneling, such as `iot:Connect`, `iot:Publish`, `iot:Subscribe`, and `iot:Receive`, as well as specific tunneling permissions like `iot:CreateTunnel`, `iot:DescribeTunnel`, and `iot:CloseTunnel`. This ensures your device can communicate securely with AWS and participate in the tunneling process, that is, pretty important for security.
You'll download the certificate and private key files during this process. These files will be placed on your IoT device to allow it to authenticate with AWS IoT Core. This step is about identity and access control, essentially, making sure only your device can do what it's supposed to do.
Step 3: Create an AWS IoT Secure Tunnel
This is where the magic happens. From your local machine, you'll use the AWS CLI to initiate a secure tunnel. You specify the IoT Thing name of your device as the destination. When you create the tunnel, AWS generates two unique client access tokens: a "source client access token" for your local machine and a "destination client access token" for your IoT device. These tokens are like temporary keys that allow the two ends to connect to the tunnel. You know, they are pretty short-lived.
You'll then run the destination client application on your IoT device, passing it the destination client access token and telling it which local port (like 22 for SSH) to forward traffic to. This client connects to AWS IoT and waits for the tunnel to become active. Meanwhile, on your local machine, you'll use the source client access token with a local proxy application provided by AWS (often a simple Python script or a small executable). This proxy will listen on a local port (e.g., 8022) and connect to the AWS Secure Tunnel endpoint, so, it's a bit like setting up a temporary bridge.
Step 4: Connect to Your Device
With the tunnel established and both the source and destination clients running, you can now use your standard SSH client to connect. You'll simply SSH to your local proxy's port, which then securely forwards your connection through the AWS IoT Secure Tunnel to your remote device. For example, if your local proxy is listening on port 8022, your command would look something like `ssh -p 8022 your_username@localhost`. It's that simple on your end, basically, once the setup is complete.
The beauty of this is that all the complex networking and security is handled by AWS. Your SSH traffic is encrypted and routed securely, without exposing your device directly to the internet. This is a powerful example of how to remotely ssh to iot device aws example, providing both convenience and strong security, that is, pretty good stuff.
Keeping Things Safe: Best Practices for Remote SSH
While enabling remote access is super helpful, keeping your devices and data safe is always the top priority. A remotely ssh to iot device aws example should always include strong security practices. Just like you'd secure your home, you need to secure your digital connections. Ignoring these steps can leave your devices vulnerable, and you know, that's something we want to avoid.
Least Privilege Access
When you set up user accounts on your IoT devices for SSH, make sure they only have the permissions they absolutely need to do their job. Don't give an account administrative rights if it only needs to check logs. This limits the potential damage if an unauthorized person somehow gains access. It's a simple idea, but very effective, so, always think about what's truly necessary.
Strong Authentication Methods
Always use SSH key pairs instead of passwords for authentication. SSH keys are much more secure and harder to guess or crack. Furthermore, protect your private keys carefully. Consider using passphrases for your private keys for an extra layer of protection. For your AWS account, enable Multi-Factor Authentication (MFA) to protect your console access and API calls. This really strengthens your security posture, that is, a critical step.
Monitoring and Logging Activity
Keep an eye on who is connecting to your devices and what they are doing. Enable logging on your SSH server and send those logs to a centralized logging service, like AWS CloudWatch Logs. This helps you detect unusual activity quickly and provides an audit trail if something goes wrong. Regularly review these logs. You know, it's like having a security camera for your digital interactions.
Regular Updates and Patches
We talked about updates for features, but security updates are even more critical. Keep your device's operating system, SSH server, and any other software up-to-date with the latest security patches. Vulnerabilities are discovered all the time, and applying patches promptly closes those potential loopholes. This is an ongoing task, but a very important one, basically, for staying safe.
Common Hurdles and Simple Solutions
Even with a clear guide, you might run into a few bumps along the way when trying a remotely ssh to iot device aws example. Don't worry, many common issues have pretty straightforward solutions. It's all part of the learning process, and you know, everyone faces these things sometimes.
Connection Issues
If you can't connect, first check your network connectivity. Is your IoT device online and able to reach AWS IoT Core? Is your local machine connected to the internet? Next, verify that the AWS IoT Secure Tunneling destination client is running correctly on your device and that your local proxy is active. Sometimes, a simple restart of these clients can resolve the problem. Also, check if your local firewall is blocking the port used by the proxy, that is, a common oversight.
Permission Problems
If your SSH connection fails with a "permission denied" error, it usually means one of two things: either your SSH key isn't correct, or the user account on the device doesn't have the right permissions. Double-check that you're using the correct private key file and that it has the right permissions (`chmod 400`). Also, ensure the user you're trying to SSH into exists on the device and has SSH access enabled. For AWS IoT permissions, review your IoT policy to make sure it includes all necessary actions for tunneling. You know, small details can make a big difference.
Device Offline or Unreachable
If your device appears offline in AWS IoT or you can't establish a tunnel, it could be a few things. The device might have lost its internet connection, or its power. Check the device's physical status first. If it's online, verify that the AWS IoT Device SDK or agent on the device is running and successfully connecting to AWS IoT Core. Sometimes, device certificates can expire or become invalid, so check those too. It's important to have a way to remotely monitor your device's online status, perhaps through AWS IoT Device Defender, to catch these issues early, basically, before they become bigger problems.
Frequently Asked Questions
People often have similar questions when they think about how to remotely ssh to iot device aws example. Here are some common ones that come up:
Q: Is SSH over AWS IoT Secure Tunneling truly safe?
A: Yes, it's designed with security in mind. The tunnel itself uses TLS encryption, and your SSH traffic is further encrypted within that tunnel. This means your data is protected during transit. Plus, it avoids opening direct inbound ports on your device, which greatly reduces its exposure to public internet threats. You know, it's a pretty robust solution.
Q: Can I use this method for non-SSH remote access, like VNC or RDP?
A: Absolutely! AWS IoT Secure Tunneling is protocol-agnostic. While we focused on SSH for this example, you can use it to tunnel other TCP-based protocols like VNC (for remote desktop), RDP, or even custom application protocols. You just specify the correct port on your device for the destination client to forward to. It's very flexible, that is, a really neat feature.
Q: What happens if my IoT device loses its internet connection during a tunnel session?
A: If the device loses its internet connection, the tunnel will break. Your SSH session will disconnect, just like any other network interruption. The tunnel will need to be re-established once the device regains connectivity and the destination client reconnects to AWS IoT. It's important to build your IoT solutions to handle intermittent connectivity gracefully, so, plan for those moments.
Final Thoughts on Remote IoT Access
Being able to remotely SSH to your IoT devices using AWS provides a powerful way to manage and troubleshoot your connected fleet. It brings together the flexibility of remote access with the robust security features that AWS provides. By following the steps we've covered and keeping best practices in mind, you can maintain control over your devices, no matter where they are, and keep them running smoothly. This kind of capability is pretty much essential for any serious IoT deployment today, you know, for peace of mind.
To learn more about managing your connected devices, explore our other guides on IoT solutions. You might also find helpful information on AWS IoT Secure Tunneling documentation directly. Keep experimenting, keep learning, and keep those devices working perfectly, basically, with confidence.
- Ellen Barkin 90s
- Somali Fiiq Wasmo Telegram
- Navy Blue Braces Teeth
- Arlyne Parrish
- Tony Romos Net Worth

Monitoring IoT Devices - AWS IoT Device Management - AWS

Understanding AWS IoT With An Example - Home Automation - Beyond App
Mastering AWS IoT Core SSH: A Comprehensive Guide To Secure IoT Device