Connecting Remote IoT To Your VPC: Keeping Things Safe
It can feel pretty unsettling when your devices warn you about an untrusted connection, or tell you they are out of date and missing important security updates. You know, that feeling when your system just isn't quite right, and you get messages like "There is a problem connecting securely to this website" or "This connection is untrusted." It's a real worry, isn't it, especially when you are trying to make sure everything works as it should? You might even find yourself trying different browsers, like MS Edge, Firefox, or Chrome, and still hitting the same wall. That's a clear sign that something fundamental needs attention, and it's a feeling many of us share, too it's almost.
Think about that feeling, but on a much larger scale, with hundreds or even thousands of small, smart devices scattered far and wide. These are your Internet of Things (IoT) gadgets, collecting all sorts of useful information, from temperature readings to equipment performance. They need to send their data back to a central hub, usually a Virtual Private Cloud (VPC) in the cloud. The big question, then, is that how do you make sure all that information travels safely, without any of those unsettling "untrusted connection" warnings popping up along the way?
This article is here to help you get a handle on just that. We'll explore the best ways to make sure your remote IoT devices connect to your VPC with strong protection, so your data stays private and your operations run smoothly. We'll talk about common hurdles, important safety measures, and some good ways to set things up. Basically, we'll help you get things back on track so your IoT network can run more securely, and you can avoid those frustrating connection problems, you know.
- Anton Daniels Restaurant
- Resorts In Tavernier Florida
- Is Darnell Nicole Still Married
- Lexiscandshop
- Jayne Marie Mansfield Movies And Tv Shows
Table of Contents
- The Challenge of Remote IoT Connections
- Foundational Security Principles for IoT-VPC Links
- Common Ways to Connect Securely
- Best Practices for a Strong IoT Security Posture
- Frequently Asked Questions (FAQ)
- Conclusion
The Challenge of Remote IoT Connections
Connecting devices that are far away to a central cloud network, like a VPC, brings a few unique difficulties. These devices are often out in the open, sometimes in places that are not physically secure, and they might be running on limited power or processing ability. This makes traditional security methods a bit tricky to put in place, you know.
For instance, an IoT sensor sitting in a remote field might not have the power to run complex encryption. Or, a device in a factory could be connected to an older network that is not set up for the newest security standards. These situations can leave gaps, which is why we sometimes see those warnings about "untrusted connections" or "security certificate problems," which can be a bit alarming, actually.
Another thing is that these devices usually connect over the public internet, which is, frankly, a bit like sending a postcard through the mail for everyone to read. Without proper protection, anyone could potentially see the data or even try to pretend to be one of your devices. So, making sure that connection is private and secure is a very big deal, and it's something we need to think about from the very start.
Why Security Matters So Much
The risks of an insecure IoT connection are quite serious. If someone manages to get into your IoT network, they could steal sensitive data, mess with how your devices work, or even use your devices to launch attacks on other systems. Imagine a smart thermostat being hacked to cause a power surge, or medical sensors sending false readings. The potential harm is pretty significant, obviously.
Beyond the direct risks, there are also consequences for your business's good name and legal standing. A data breach can lead to a loss of trust from customers and hefty fines from regulators. That's why making sure your IoT connections are safe isn't just a technical task; it's a fundamental part of keeping your operations sound and your business reputable, and it's pretty important, really.
Moreover, those "out of date" messages we talked about earlier are not just annoying pop-ups. They are critical warnings. An outdated device or system often has known weaknesses that bad actors can easily exploit. Keeping everything current is a basic, yet incredibly important, step in protecting your entire setup, and it's a good habit to get into, basically.
Foundational Security Principles for IoT-VPC Links
To build a really strong connection between your IoT devices and your VPC, you need to start with some basic safety ideas. These are like the building blocks for any good security plan. We're talking about making sure only the right devices can connect, that their messages are private, and that everyone only has the permissions they truly need.
It's a bit like setting up a secure clubhouse for your data. You want to know who is trying to get in, make sure their conversations inside are private, and give each person only the keys they need for their specific job. Without these basics, any fancy security tools you add later might not do much good, you know.
These principles help address those "untrusted connection" problems directly. If a device can't prove who it is, or if its messages are not properly sealed, then the connection should, quite rightly, be flagged as untrusted. So, getting these foundations right is the first big step towards a dependable and safe IoT system, and it's pretty simple when you think about it, right?
Identity and Authentication: Making Sure It's the Right Device
The first thing you need to know is that the device trying to connect is actually one of your devices, and not some impostor. This is called identity and authentication. For IoT, this often means giving each device a unique digital identity, like a special certificate or a secure key. When a device tries to connect, it presents this identity, and your VPC checks if it's legitimate.
This is where those "security certificate problems" mentioned in your text come into play. If a device presents a certificate that isn't valid, or wasn't issued by a trusted authority, then the connection should absolutely be rejected. It's a fundamental check, like asking for ID at a secure entry point, and it's incredibly important, you know.
Many cloud providers offer services to manage these device identities, making it easier to give out, revoke, and update certificates for thousands of devices. Using strong, unique identities for each device, and regularly checking them, helps prevent unauthorized access to your network. It's a bit like giving each device its own secure passport, and it's actually quite clever.
Data Encryption: Keeping Information Private
Once you know it's the right device, the next step is to make sure that whatever information it sends is kept private. This is where encryption comes in. Encryption scrambles your data into a secret code while it travels, and then it gets unscrambled only when it reaches its intended destination. This way, even if someone intercepts the data, they can't understand it.
Think of it like putting your important message in a locked box before sending it. Only the person with the right key can open the box and read the message. For IoT, this often means using protocols like TLS (Transport Layer Security) or DTLS (Datagram Transport Layer Security) for communication, which are pretty standard, and honestly, very effective.
Ensuring that all data, both from the device to the cloud and back again, is encrypted is a must-do. This protects sensitive information from being spied on and helps maintain the integrity of the data. It's a core defense against many types of attacks, and it helps prevent those "problem connecting securely" messages that suggest data might be exposed, you know.
Access Control: Who Gets to Do What
Even after a device is authenticated and its data is encrypted, you still need to control what that device is allowed to do. This is access control. An IoT sensor, for example, should only be allowed to send data, not to change settings on other devices or access sensitive parts of your VPC. This idea is often called "least privilege."
You give each device or group of devices only the minimum permissions they need to perform their job, and nothing more. This limits the damage if a device ever gets compromised. If a hacker takes over a temperature sensor, they won't be able to, say, shut down a critical system if that sensor never had the permission to do so, which is pretty sensible, right?
Cloud providers offer robust Identity and Access Management (IAM) tools that let you define very precise rules for what each device can and cannot do within your VPC. Regularly reviewing these permissions is also a smart move, just to make sure they are still appropriate. It's a bit like making sure everyone has only the keys to the rooms they actually need to enter, and it's a very good practice.
Common Ways to Connect Securely
Now that we've covered the basic principles, let's talk about the practical ways you can set up these secure connections. There are several methods, and the best choice often depends on things like how many devices you have, where they are located, and how much data they send. Each method has its own strengths, you know.
The goal here is to create a secure tunnel or pathway between your remote IoT devices and your VPC. This tunnel should protect the data in transit and make sure only authorized traffic gets through. It's about building a dependable bridge that can withstand various challenges, and it's pretty exciting, actually, to see how it all comes together.
We'll look at a few popular approaches, from setting up virtual private networks to using dedicated physical connections, and even how application-level security plays a part. Understanding these options will help you pick the right tools for your specific needs, and it's a pretty important step in getting your IoT system up and running safely, so.
Using Virtual Private Networks (VPNs)
VPNs are a very common way to create a secure, encrypted connection over a public network, like the internet. For IoT, you can set up a Site-to-Site VPN between your remote IoT gateway (a device that collects data from many IoT sensors) and your VPC. This creates a secure tunnel, and all traffic passing through it is encrypted.
It's like building a private road through a public park. Only traffic from your designated entry points can use it, and everything on that road is hidden from view. This is great for locations with many devices, like a factory floor or a large office building, where you want all devices in that location to use the same secure path, and it's quite efficient, too it's almost.
Another option is a Client VPN, where individual IoT devices or small groups of devices establish their own secure connection to the VPC. This might be suitable for devices that are very spread out and don't have a central gateway. Both types of VPNs help prevent those "untrusted connection" messages by ensuring data privacy and integrity from the start, and they are pretty reliable, honestly.
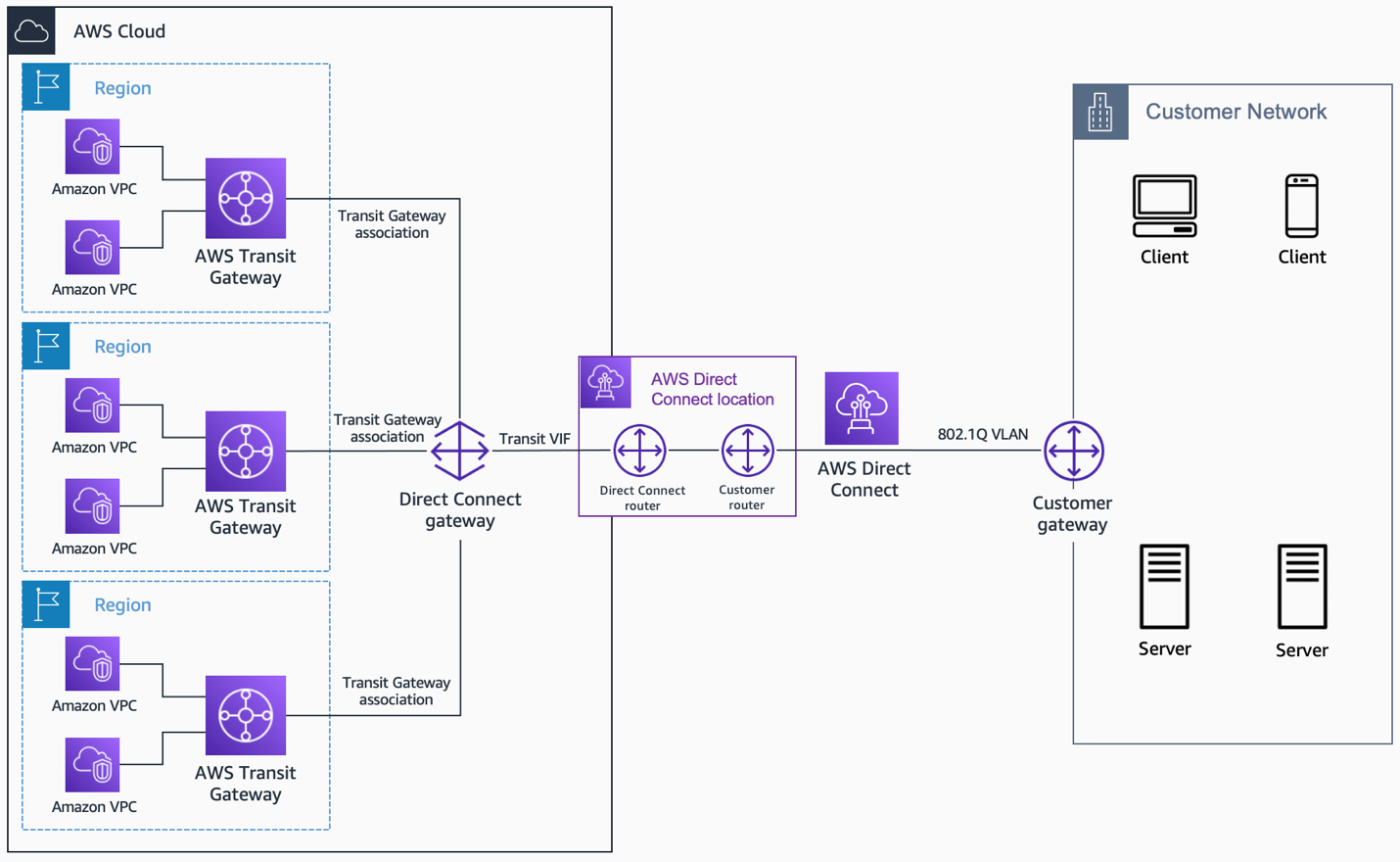
Direct or Dedicated Connections
For situations where you need extremely high bandwidth, very low delay, or the utmost security, a direct or dedicated connection might be the answer. Services like AWS Direct Connect or Azure ExpressRoute create a private, physical network link between your on-premises location and your cloud VPC. This bypasses the public internet entirely.
Imagine having your own private, super-fast highway directly connecting your IoT operations center to your cloud data center. There are no other cars on this road, and it's built just for your traffic. This is ideal for large-scale industrial IoT deployments or situations where data sensitivity is extremely high, and you need maximum performance and protection, you know.
While these connections can be more costly to set up, they offer unparalleled security and performance benefits. They completely remove the risk of public internet exposure for your main data streams, significantly reducing the chances of "untrusted connection" issues arising from network interception. It's a premium solution, and it's pretty powerful, really.
Secure Tunneling and Protocol Security
Beyond network-level VPNs, you can also secure connections at the application level using secure tunneling protocols. This often involves using TLS (Transport Layer Security) or DTLS (Datagram Transport Layer Security) directly on the IoT device itself. These protocols encrypt the data payload and ensure that the communication is happening with the intended server, verifying its identity.
This is particularly important for devices that might not be able to support a full VPN client due to their small size or limited processing power. Each message or data stream is individually secured. It's like putting each individual letter into its own locked envelope before mailing it, even if the mail carrier is on a public road, which is pretty clever, you know.
Many IoT platforms and services are built to use these secure protocols by default, often relying on digital certificates for device authentication. This directly addresses the "security certificate presented by this website is not secure" problem, as proper certificate management is at the heart of these protocols. Ensuring your devices use up-to-date certificates and strong cipher suites is key, and it's a very good way to protect your data, so.
Best Practices for a Strong IoT Security Posture
Having the right connection methods is just one part of the puzzle. To truly keep your remote IoT devices and VPC safe, you need to follow a broader set of good habits and practices. It's an ongoing effort, not a one-time setup. Think of it like keeping your home secure; you don't just lock the doors once and forget about it, you know.
These practices help address the root causes of many security problems, including those "out of date" warnings and general connection issues. A proactive approach means you're always a step ahead, rather than reacting to problems after they happen. It's about building resilience into your entire system, and it's pretty important, actually.
We'll cover things like keeping your systems updated, organizing your network carefully, watching for unusual activity, and having a plan for when things go wrong. These steps, when put together, create a much more secure environment for your IoT operations, and they are pretty straightforward to put into action, too it's almost.
Regular Updates and Patching
This is perhaps one of the most critical, yet often overlooked, aspects of security. Just like your personal computer needs "important security and quality updates," so do your IoT devices and the systems they connect to in your VPC. Software and firmware updates often contain fixes for newly discovered security weaknesses.
Leaving devices or software outdated is like leaving a window open for someone to climb through. Bad actors are constantly looking for known vulnerabilities in older versions of software. Regularly applying patches closes these windows and makes it much harder for them to get in. It's a simple step that makes a huge difference, and it's a very good habit to maintain, obviously.
Develop a plan for how you'll update your remote IoT devices. This can be challenging for devices that are hard to reach, but it's essential. Consider over-the-air (OTA) update mechanisms provided by IoT platforms. Keeping your systems current is a primary defense against many common attacks, and it directly addresses the "your device is at risk because it's out of date" problem, you know.
Network Segmentation and Firewall Rules
Within your VPC, it's a good idea to divide your network into smaller, isolated sections. This is called network segmentation. You can put your IoT devices in one section, your data processing in another, and your management tools in a third. Then, you use firewall rules (like security groups and network access control lists) to control exactly what traffic can pass between these sections.
Think of your VPC as a large building. Instead of one big open space, you create separate rooms with locked doors. If someone manages to get into one room (say, an IoT device is compromised), they can't easily move to other, more sensitive rooms without going through another locked door. This limits the spread of any potential breach, which is pretty smart, right?
Carefully configure your firewall rules to allow only the necessary communication paths. For instance, IoT devices should only be able to talk to the IoT ingestion service in your VPC, not directly to a database or a web server. This principle of "least privilege" applies to network traffic too, and it's a very effective way to contain risks, so.
Monitoring and Alerting
You can't protect what you don't see. Setting up robust monitoring for your IoT devices, their connections, and your VPC resources is vital. This means collecting logs, tracking network traffic, and looking for any unusual patterns or activities. For example, if a device suddenly starts sending a huge amount of data, or tries to connect from an unexpected location, that could be a sign of trouble.
Having alerts in place means you get notified immediately if something suspicious happens. This could be an alert for failed connection attempts, unusual data volumes, or changes to security settings. Quick detection allows you to respond to threats before they cause significant damage, and it's pretty much like having a watchful eye on everything, you know.
Cloud providers offer a range of logging and monitoring services that can be integrated with your IoT platform and VPC. Regularly reviewing these logs and tuning your alerts helps you stay on top of your security posture. It's a continuous process of observation and adjustment, and it's a very important part of keeping things safe, honestly.
Incident Response Planning
Even with the best security measures, problems can still happen. That's why having a clear plan for what to do when a security incident occurs is so important. This is your incident response plan. It outlines the steps to take if a device is compromised, a connection is breached, or data is stolen.
Your plan should cover things like how to identify the problem, how to contain it (e.g., disconnecting a compromised device), how to remove the threat, how to recover your systems, and how to learn from the incident to prevent future ones. It's a bit like having a fire drill; you hope you never need it, but you're prepared if you do, and it's pretty comforting to have, actually.
Regularly testing your incident response plan helps ensure that everyone knows their role and that the steps are effective. This readiness can significantly reduce the impact of a security event and help you get back to normal operations much faster. It's a proactive step that builds resilience, and it's a very smart thing to put in place, you know.
Frequently Asked Questions (FAQ)
How can I tell if my IoT device connection is truly secure?
You can check for a few things. First, make sure the connection uses strong encryption, like TLS or DTLS, which you can often see in your device's configuration or logs. Look for proper certificate validation, meaning the device is checking the server's identity, and the server is checking the device's identity. Also, monitor your network for any unusual traffic patterns or failed authentication attempts. If you're seeing messages about "untrusted connections" or "security certificate problems," that's a clear sign something needs attention, and it's pretty important to investigate, obviously.
What's the biggest security risk for remote IoT devices?
Arguably, one of the biggest risks is having outdated software or firmware on the device. Many security problems come from known weaknesses that could have been fixed with an update. Another major risk is weak authentication, where devices use easy-to-guess passwords or don't verify their identity properly. These issues make it much easier for unauthorized people to get into your system, and it's a very common problem, you know.
Can I use my existing VPN for IoT devices?
Yes, in many cases, you can use your existing VPN setup, especially if it's a Site-to-Site VPN connecting a remote location to your VPC. However, you need to make sure your IoT devices or their gateways are configured to use that VPN. For very small or resource-limited IoT devices, a full VPN client might be too much for them to handle. In those situations, you might need to rely more on application-level security like TLS, or use an IoT gateway that handles the VPN connection for a group of devices, which is pretty practical, actually. Learn more about secure connections on our site.
Conclusion
Making sure your remote IoT devices connect to your VPC with strong protection is a big deal, and it's something that really needs careful thought. We've seen how common problems like "untrusted connections" and "out-of-date systems" can cause worry, and how crucial it is to get these basic security measures right. By focusing on strong identity checks, keeping data private through encryption, and carefully controlling who can do what, you build a solid foundation.
Choosing the right way to connect, whether it's through VPNs, dedicated links, or secure tunneling, helps create those safe pathways for your data. But it doesn't stop there. Keeping everything updated, organizing your network carefully, watching for any strange activity, and having a plan for when things go wrong are all ongoing tasks that keep your system safe. These steps help you avoid those frustrating security warnings and ensure your IoT operations run smoothly and securely, you know.
Taking these steps helps you gain peace of mind, knowing your valuable IoT data is protected and your operations are secure. It's about being proactive and thoughtful in how you build and manage your connections. So, take a look at your current setup, see where you can make things safer, and get your IoT network running with the protection it deserves. You can also link to this page for more detailed security information.
- Emily Skeggs Movies And Tv Shows
- Golden Blonde Hair
- Why Did Joe Armacost Leave Dan Bongino
- Wnba Ratings Without Clark
- Laura Mercier Animal Testing

Securely Connect Remote IoT VPC Raspberry Pi AWS: A Comprehensive Guide

Securely Connect Remote IoT VPC Raspberry Pi: Free Download For Windows
Securely Connect Remote IoT VPC AWS Not Working Windows: Comprehensive